Case Study
Data Leaks and Customer Trust Erosion – Uber (2016)
6 Key IT Leadership Lessons from a $148M Privacy Crisis
What Happened: The 2016 Uber Data Breach and Its Hidden Fallout
In 2016, Uber suffered a major data breach that exposed the personal information of 57 million users and drivers globally. The stolen data included names, email addresses, and phone numbers of riders, along with the driver’s license numbers of over 600,000 drivers.
But what made the situation worse was Uber’s decision to conceal the breach. Rather than disclose the incident, the company paid the hackers $100,000 to delete the data and stay quiet. This intentional cover-up lasted over a year and only came to light in late 2017, triggering legal investigations and public outrage.

Financial and Reputational Damage
The consequences of the breach—and Uber’s concealment—were severe:
- $148 million in settlements with U.S. states over violation of breach notification laws
- Severe loss of consumer and driver trust
- Legal scrutiny by regulators in multiple jurisdictions
- Increased reputational risk that hurt valuation and IPO readiness
Uber’s incident became a cautionary tale for companies prioritizing short-term image over transparent security practices.
Leadership Response and Strategic Overhaul
The newly appointed executive team, following the breach disclosure, led a comprehensive transformation:
- Global Security Audit: All systems, APIs, and cloud storage were reviewed for vulnerabilities.
- Leadership Changes: A new Chief Information Security Officer (CISO) was brought in to rebuild the security culture.
- Data Encryption and Governance: The company deployed advanced encryption protocols and began strict management of access controls.
- Transparent Policy Reset: Uber committed to proactive disclosure and updated its privacy policies in accordance with GDPR and U.S. regulations.
Implementation Timeline
- Month 1–3: Breach disclosure, investigations, and initial damage control
- Month 4–9: Internal audits, leadership reshuffles, security tool deployment
- Month 10–12: Training, policy updates, and trust-building campaigns
This year-long effort was central to Uber’s mission to rebuild both its systems and its stakeholder relationships.
Competitive Advantage Gained
- Trust-by-Design Approach: Data security features became product highlights in app updates and privacy notices.
- Enhanced Transparency: Public-facing security updates helped rebuild driver and rider confidence.
- Enterprise Readiness: Improved governance practices made Uber more appealing to regulators, partners, and enterprise customers.
What IT Leaders Must Learn: 6 Strategic Data Protection and Trust Measures
1. Prioritize Transparent Breach Disclosure Policies
What Went Wrong:
Best Practices for IT Leaders:
- Immediate Disclosure Plans: Establish breach notification timelines in line with laws (e.g., 72 hours under GDPR).
- Pre-approved Communications: Prepare legal and PR messaging templates to use during incidents.
- Transparency Culture: Treat breach reporting as a trust-building opportunity, not a liability.
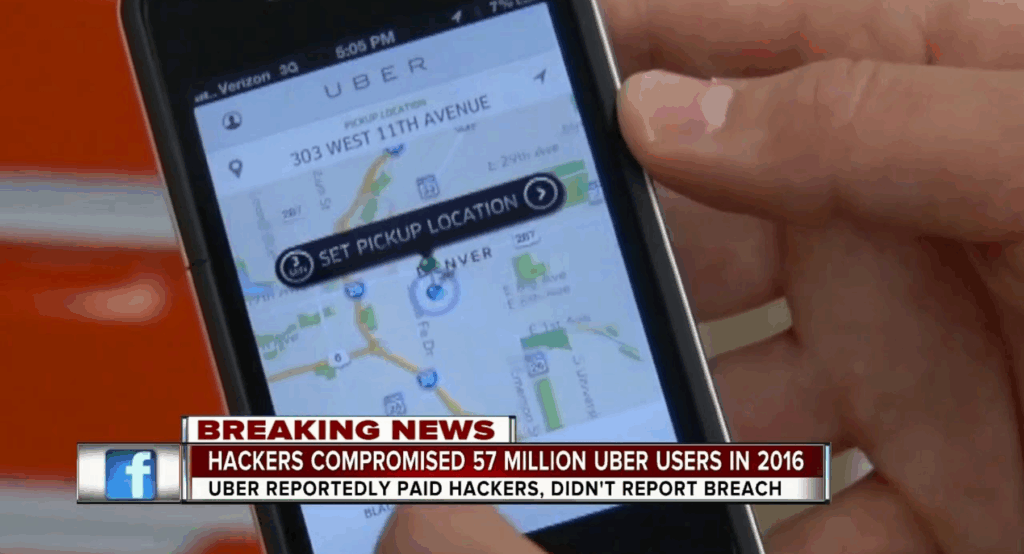
image source- ABC Action News
2. Conduct a Full-Spectrum Security Audit Post-Incident
What Went Wrong:
Best Practices for IT Leaders:
- End-to-End System Review: Evaluate all internal systems, cloud environments, and third-party integrations.
- Access Control Reviews: Identify accounts with excessive privileges and implement least-privilege models.
- API and Storage Scanning: Detect unprotected data, misconfigured S3 buckets, or open access points.
3. Appoint and Empower a Modern Security Leadership Team
What Went Wrong:
Best Practices for IT Leaders:
- Hire a CISO with Board Access: Make security leadership part of strategic decision-making.
- Create a Security Operations Center (SOC): Monitor threats in real-time with automated detection.
- Establish Cross-Team Security Champions: Embed experts in engineering, legal, and product teams.
4. Encrypt All Sensitive Data at Rest and in Transit
What Went Wrong:
Best Practices for IT Leaders:
- Data-at-Rest Encryption: Use AES-256 encryption across all databases and backups.
- Data-in-Transit Encryption: Secure traffic with TLS 1.3 and VPNs for internal systems.
- Key Management: Use centralized, policy-driven encryption key systems with multi-factor approval.
5. Formalize Data Governance Policies and Role-Based Access
What Went Wrong:
Best Practices for IT Leaders:
- Data Classification: Label data (e.g., PII, PHI, Confidential) to apply tailored protections.
- Role-Based Access Controls (RBAC): Ensure only those who need access can retrieve data.
- Regular Audits and Logs: Track all access events and review them for anomalies monthly.
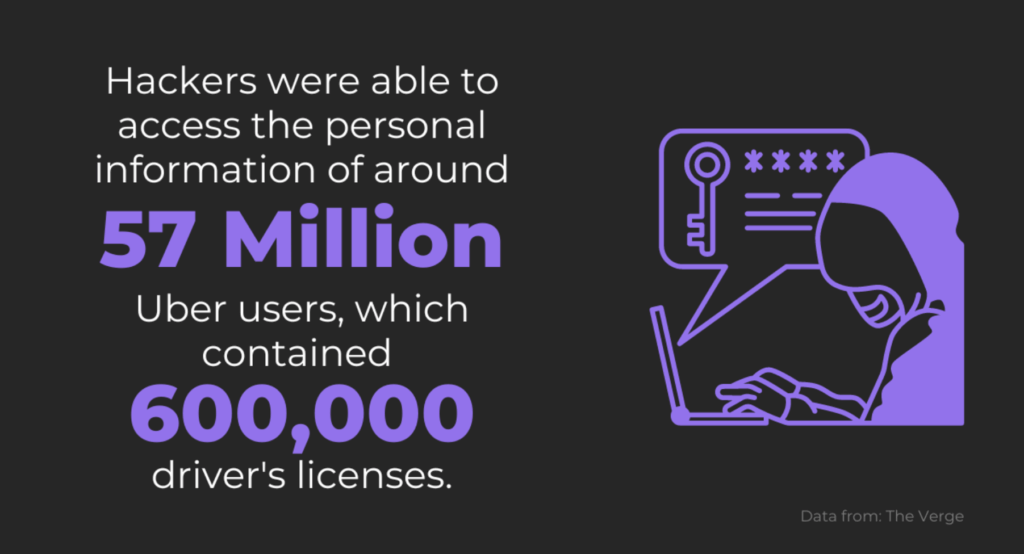
image source- Shakebugs
6. Train Employees and Build a “Trust-First” Culture
What Went Wrong:
Best Practices for IT Leaders:
- Mandatory Security Awareness Training: Conduct regular training with up-to-date attack examples.
- Gamify Compliance: Make security training interactive and reward compliance milestones.
- Promote a Trust-First Ethos: Make privacy, security, and transparency part of the corporate mission.
Conclusion: Trust is Earned, Not Recovered Overnight
Uber’s 2016 breach did more than expose data—it exposed the cost of concealment and the lack of a security-first mindset. But with strategic leadership changes, robust encryption, and cultural reform, Uber demonstrated how trust can be rebuilt.
For today’s IT leaders, the lessons are critical:
- Act fast, but act transparently
- Empower security leadership
- Make trust your brand, not just your compliance goal

Let YALLO Solve Your Talent Challenges
Struggling with complex IT needs? Partner with YALLO for tailored solutions that reduce costs, improve quality, and deliver results. Book an appointment today to discuss how we can help your business thrive.














