Case Study
Insider Data Theft – Capital One (2019)
6 Cloud Security and Governance Lessons for IT Leaders
What Happened: The Capital One Insider Breach
In 2019, Capital One suffered a massive data breach when a former AWS employee exploited a misconfigured web application firewall (WAF) to gain unauthorized access to customer data stored in the cloud. The attack compromised sensitive information for over 100 million individuals in the U.S. and Canada, including:
- Names and contact details
- Credit scores
- Social Security and bank account numbers (for a subset)
The breach was particularly alarming because it highlighted vulnerabilities in cloud infrastructure, as well as the damage a technically sophisticated insider could cause.

image source- summitcl
Financial and Legal Consequences
- $80 million in fines issued by U.S. regulators due to failure in risk assessment and cloud configuration
- Cost of remediation including forensic investigation, legal settlements, and customer support
- Brand damage in a tightly regulated financial sector that depends on consumer trust
Leadership Response: A Strategic Cloud Security Overhaul
Capital One launched a company-wide transformation aimed at reinforcing its data and cloud security:
- Restructured Security and Governance Teams: Created dedicated units for cloud governance and access control.
- Access Control Hardening: Implemented role-based access and privileged account monitoring.
- Cloud-Native Security Tools: Deployed advanced intrusion detection and cloud misconfiguration management systems.
- Cultural Reset: Instilled a “secure-by-design” mindset across engineering and product teams.
Implementation Timeline
- Month 1–3: Forensic investigation, public disclosure, risk triage
- Month 4–9: Team restructuring, new controls, and tool deployment
- Month 10–12: Internal training, audit readiness, and updated cloud policies
Competitive Advantage Achieved
Post-breach, Capital One pivoted to proactive transparency, using its enhanced cloud security posture as a market differentiator:
- Promoted secure cloud-native architecture in industry forums
- Boosted confidence among fintech partners and enterprise clients
- Won recognition for robust adoption of zero-trust models and DevSecOps integration
What IT Leaders Must Learn: 6 Strategic Cloud and Insider Risk Measures
1. Secure Cloud Configurations with Continuous Monitoring
What Went Wrong:
Best Practices for IT Leaders:
- Cloud Security Posture Management (CSPM) tools to detect risky misconfigurations
- WAF Configuration Audits: Regular reviews of firewall and gateway rule sets
- Automated Policy Enforcement: Use Infrastructure as Code (IaC) with embedded security templates
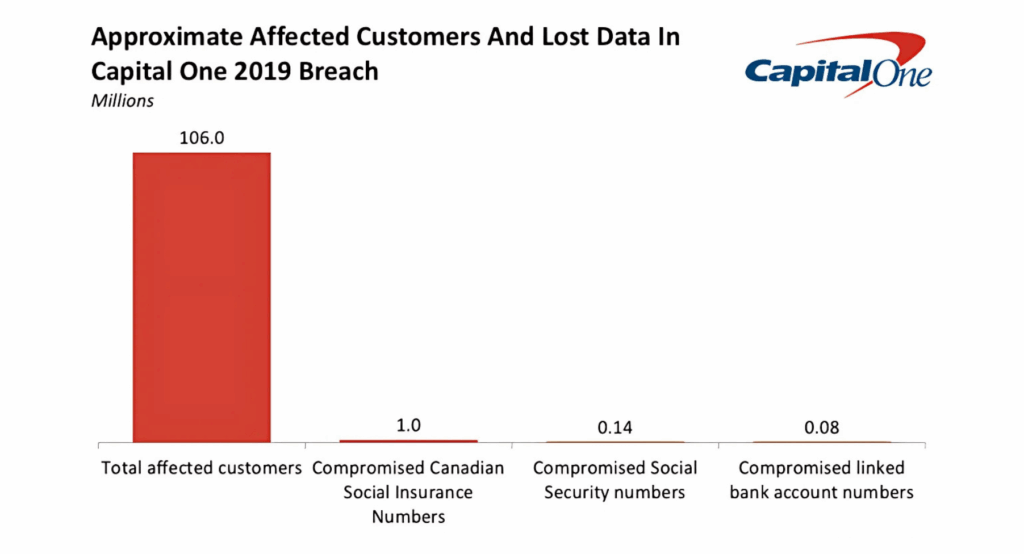
image source- Company filings, 2019
2. Enforce Least-Privilege Access and RBAC
What Went Wrong:
Best Practices for IT Leaders:
- Role-Based Access Control (RBAC) with strict scope definitions
- Just-In-Time Access (JIT): Temporary privilege escalation with time limits
- Privileged Access Management (PAM) platforms for high-risk accounts
3. Monitor for Insider Threats Using Behavior Analytics
What Went Wrong:
Best Practices for IT Leaders:
- User and Entity Behavior Analytics (UEBA) to flag anomalies in access or data transfer
- Data Loss Prevention (DLP) tools to alert on bulk data exfiltration
- Internal Threat Simulations: Run mock insider scenarios to test detection readiness
4. Embed Security into Cloud DevOps (DevSecOps)
What Went Wrong:
Best Practices for IT Leaders:
- Security as Code: Incorporate scanning into CI/CD pipelines
- Code Reviews for Cloud Templates: Vet Terraform, CloudFormation, and Kubernetes YAMLs
- Security Gatekeeping: Automated policies to block misconfigured deployments
5. Conduct Cloud-Specific Risk Assessments
What Went Wrong:
Best Practices for IT Leaders:
- Risk Matrix by Cloud Asset: Score impact and likelihood for every S3 bucket, IAM policy, or Lambda function
- Cloud Threat Modeling: Regularly analyze attack paths specific to microservices and APIs
- Third-Party Cloud Audits: External reviews to uncover blind spots

6. Create a Culture of Cloud Security Awareness
What Went Wrong:
Best Practices for IT Leaders:
- Cloud Security Bootcamps: Train devs on secure API, secrets, and identity practices
- Live Simulations: Incident response drills involving cloud breach scenarios
- KPIs for Security Hygiene: Tie team success to patching rates, alert response times, and misconfiguration resolution
Conclusion: From Cloud Vulnerability to Cloud Leadership
The 2019 Capital One breach revealed that cloud infrastructure, while scalable and agile, is also uniquely vulnerable without proper governance. Yet, the company’s decisive response—grounded in strategic IT leadership—transformed crisis into credibility.
For IT and security leaders, this case reinforces the need to:
- Design cloud systems with resilience and oversight
- Detect not just outside threats, but internal abuse
- Make security a foundational layer, not an afterthought
With cloud adoption accelerating, Capital One’s journey offers a crucial roadmap for secure digital transformation.

Let YALLO Solve Your Talent Challenges
Struggling with complex IT needs? Partner with YALLO for tailored solutions that reduce costs, improve quality, and deliver results. Book an appointment today to discuss how we can help your business thrive.














