Case Study
Mega-Breach with Eye-Watering Costs – Equifax (2017)
6 Vital IT Leadership Lessons from the Crisis
What Happened: The Anatomy of the Equifax Data Breach
In mid-2017, Equifax, one of the largest U.S. credit reporting agencies, experienced a catastrophic data breach that exposed sensitive information of approximately 147 million people. The attackers exploited a known vulnerability in the Apache Struts web application framework (CVE-2017-5638), which Equifax had failed to patch for over two months after the fix was available.
Attackers gained access to databases containing highly sensitive personal data such as:
- Full names
- Social Security numbers
- Birth dates
- Addresses
- Driver’s license numbers
- Credit card details for over 200,000 individuals
Shockingly, the breach persisted for 76 days before detection, giving hackers ample time to steal massive volumes of data. Once discovered, Equifax waited six additional weeks before notifying the public, further damaging its credibility.

Image source- 8newsnow
Financial and Reputational Repercussions
The financial impact was staggering:
- $700 million in settlements and regulatory fines (as per FTC, CFPB, and 50 states)
- Long-term costs in litigation, loss of consumer trust, and stock price declines
- Congressional hearings and reputational fallout among consumers and partners
The incident has since become a textbook example of how cyber negligence can jeopardize an entire enterprise.
What IT Leaders Must Learn: Precautions to Prevent Future Breaches
The Equifax breach wasn’t due to a lack of technology—it was a systemic failure in leadership, process discipline, and risk management. Below are six expanded enterprise security precautions IT leaders must prioritize:
1. Build a Robust Vulnerability Management Program
What Went Wrong:
Equifax failed to patch a publicly disclosed vulnerability for over two months—despite an alert from the U.S. Computer Emergency Readiness Team (US-CERT).
Best Practices for IT Leaders:
- Automated Scanning: Deploy continuous vulnerability scanning tools to identify weaknesses across the environment.
- Patch Prioritization: Use CVSS scores to rank vulnerabilities and prioritize critical ones immediately.
- Maintenance Windows: Schedule regular patching windows to ensure minimal delay in implementing updates.
- Third-Party Audits: Have external experts periodically review your patching lifecycle for blind spots.
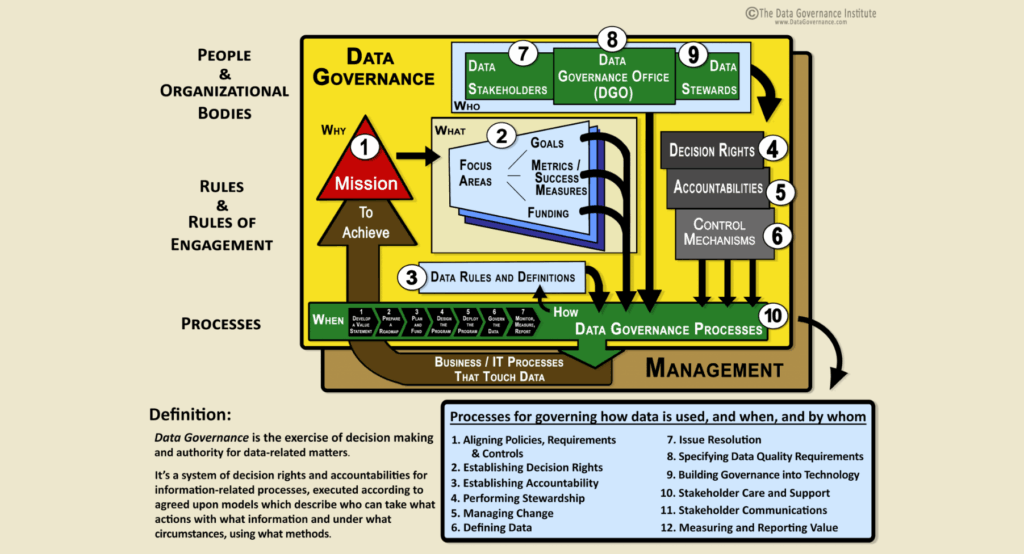
image source- datagovernance
2. Enforce Strong Data Governance and Ownership
What Went Wrong:
There was no centralized oversight of sensitive data or clear responsibility for its protection.
Best Practices for IT Leaders:
- Appoint a Chief Data Officer (CDO): This role ensures accountability for data quality, compliance, and security.
- Create a Data Governance Council: A cross-functional team responsible for policy enforcement, audit, and strategic oversight.
- Implement Role-Based Access Controls (RBAC): Only authorized individuals should access sensitive data, with regular access reviews.
- Data Classification: Label and segment data based on its sensitivity (e.g., public, internal, confidential, restricted).
3. Invest in Continuous Monitoring and Threat Detection
What Went Wrong:
Best Practices for IT Leaders:
- SIEM Platforms: Use tools like Splunk or IBM QRadar to aggregate and analyze logs for suspicious activity.
- Intrusion Detection and Prevention Systems (IDPS): These can flag anomalous behavior and unauthorized access in real-time.
- Behavioral Analytics: Machine learning-based tools can detect deviations in user or system behavior that may indicate a breach.
- 24/7 SOC Team: Have an in-house or outsourced Security Operations Center to monitor alerts and escalate incidents.
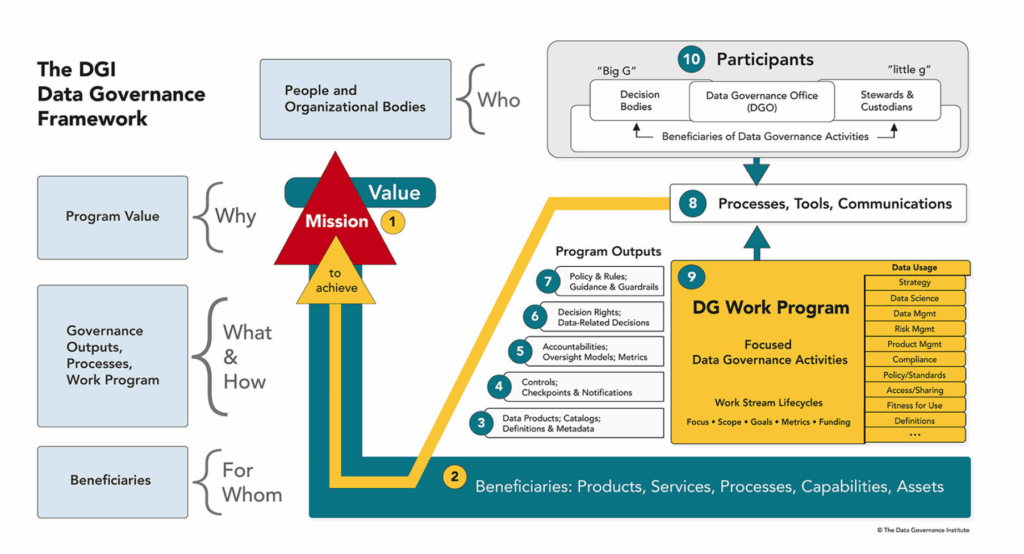
image source- datagovernance
4. Promote a Cybersecurity-First Organizational Culture
What Went Wrong:
Best Practices for IT Leaders:
- Executive Support: Ensure cybersecurity is championed by the board and C-suite, not just IT.
- Security Awareness Training: Regularly train staff on phishing, secure behavior, and data handling.
- Gamified Learning: Use engaging platforms that test employee responses to simulated attacks.
- Recognition & Accountability: Incentivize secure practices and create clear penalties for negligent behavior.
5. Develop and Regularly Test Your Incident Response Plan
What Went Wrong:
Best Practices for IT Leaders:
- Incident Response Team (IRT): Form a dedicated team with clearly defined roles (legal, PR, tech, HR, etc.).
- Playbooks for Attack Types: Maintain specific response protocols for DDoS, ransomware, data theft, insider threats, etc.
- Tabletop Exercises: Simulate breach scenarios to test response agility and improve readiness.
- Breach Disclosure Policy: Have a clear, pre-approved communication strategy to notify regulators, stakeholders, and the public.
6. Harden Your Applications and APIs
What Went Wrong:
Best Practices for IT Leaders:
- Secure Development Lifecycle (SDLC): Integrate security checkpoints into every phase of software development.
- Static and Dynamic Code Analysis: Test both compiled and running code for vulnerabilities.
- Web Application Firewalls (WAF): Filter and monitor HTTP traffic to prevent injection attacks, XSS, and more.
- API Security Gateway: Authenticate, encrypt, and rate-limit API calls—especially those handling personal data.
Conclusion: Strategy Over Technology
The Equifax breach illustrates that enterprise security begins with discipline, leadership, and accountability. Technology alone can’t prevent breaches without strong governance, continuous vigilance, and a proactive culture of cybersecurity. IT leaders must move from reactive firefighting to strategic risk prevention.
By embedding cybersecurity into organizational DNA, companies can turn risk into resilience—and safeguard the trust of millions.

image source- sentinelone

Let YALLO Solve Your Talent Challenges
Struggling with complex IT needs? Partner with YALLO for tailored solutions that reduce costs, improve quality, and deliver results. Book an appointment today to discuss how we can help your business thrive.














